- Top seven free cell phone tracking software
- Track Google cell phone using Mobile defense
- Best free cell phone tracking software Glympse
- Free GPS cell phone tracker – Map My Tracks
- Free cell phone tracker software – SOS Tracker
- Free cell phone tracking software – GPSed
- How to track your cell phone using InstaMapper
- Plan B – Find my phone app for Android
- Track cell phone or PC online using Profone trackers
- Free cell phone GPS logger for BlackBerry devices
Bookmarks
naa adda
Categories
- christmas (1)
- Easter (1)
- god photos (1)
- heats tips (9)
- home (2)
- jntuk (1)
- jokes (1)
- lab programs (1)
- m.tech (2)
- Materials (1)
- mba (1)
- MJ Club (3)
- mobile recharge (1)
- movies (1)
- PPTs (1)
- projects (3)
- SONGS (30)
- Teating knowledge (7)
- TECHNICAL FORUM (49)
Archive
-
▼
2012
(126)
-
▼
May
(49)
- How to use mobile tracking system
- moreeeee
- shotcuts to facebook users in telugu lang
- Facebook Tries, Tries Again on a Smartphone
- In Coal Country, the Fight for an Industry
- HOW TO SPY A MOBILE PHONE?
- Love Journey (2012)
- Coming Up! W.TEC Technology Camp for Teenagers
- Engineer Details Plans to Build a Real, Burj-Dubai...
- Ninnu Choosthe Love Vasthundi (2012)
- How It Works: Underground Robot Library
- YOUTUBE NEW INTERFACE WITH AUDIO EDITING
- Neeku Naaku Dash Dash (2012)
- hack-facebook-password-newest-version
- How To Protect USB With Password
- Tops Gift Ideas For Mom
- Top 10 Tips To Keep Your Mac Secure
- blog review www.mptbcse.blogspot.in
- పీజీలో ప్రవేశానికి ఇవీ పరీక్షలు
- అభిరుచితో అందలం...ఇంజినీరింగ్.....,!!!!!
- ppyyyyyy mothers day to ur all mom's from my sides
- testing of s/w knowlerge
- V Model vwery imp testing
- Teating knowledge
- HAPPY M0TH€RS DAY MAMA
- Michael Jackson Filipino Fans Club
- VirtualMedicalHome
- mj photos
- joke
- 10 Brilliant Technology Visionaries
- HOW TO VIEW PASSWORDS BEHIND ASTERISKS why?
- Allu Arjun's Upcoming Film " JULAI (2012) " Super ...
- Endukante Premanta..
- useing of browsers
- Interview Tips: Group Discussion Interview Tips
- REMOVE VIRUSES FROM USB DRIVE EASILY & EFFECTIVELY
- FEDORA 16 DESKTOP EDITION
- Install Windows 7 From a USB Flash Drive or USB Ha...
- The Truth About Hydration in the Heat
- How to Adapt to the Heat for Summer Runs
- 8 Tips for Running in Hot Weather
- Like for Heaven!! Pass for Hell :(
- Premalo Padithe (2012) Telugu Mp3 Songs Free Download
- SONGS
- Low Calorie Snacks
- Pressure
- The Human Element
- Coming Up! W.TEC Technology Camp for Teenagers
- Large New NIH Study Finds That Cell Phone Use Does...
-
▼
May
(49)
Total Pageviews
Thursday, May 31, 2012
Wednesday, May 30, 2012
Facebook Tries, Tries Again on a Smartphone
Published :
7:34 PM
Author :
REVANTH cityboy from cse
Facebook Tries, Tries Again on a Smartphone
By NICK BILTON | May 27, 2012, 1:53 PM 59 Comments
Can a software company build its own smartphone? We may find out soon.
This past week, Google completed its acquisition of the hardware maker Motorola Mobility for $12.5 billion, which could lead to the search giant’s making its own smartphone. But another software titan might be getting into the hardware game as well: Facebook.
Employees of Facebook and several engineers who have been sought out by recruiters there, as well as people briefed on Facebook’s plans, say the company hopes to release its own smartphone by next year. These people spoke only on the condition of anonymity for fear of jeopardizing their employment or relationships with Facebook.
The company has already hired more than half a dozen former Apple software and hardware engineers who worked on the iPhone, and one who worked on the iPad, the employees and those briefed on the plans said.
This would be Facebook’s third effort at building a smartphone, said one person briefed on the plans and one who was recruited. In 2010, the blog TechCrunch reported that Facebook was working on a smartphone. The project crumbled after the company realized the difficulties involved, according to people who had worked on it. The Web site AllThingsDreported last year that Facebook and HTC had entered a partnership to create a smartphone, code-named “Buffy,” which is still in the works.
 Rajanish Kakade/Associated Press
Rajanish Kakade/Associated Press
Now, the company has been going deeper into the process, by expanding the group working on Buffy, and exploring other smartphone projects too, creating a team of seasoned hardware engineers who have built the devices before.
One engineer who formerly worked at Apple and worked on the iPhone said he had met with Mark Zuckerberg, Facebook’s chief executive, who then peppered him with questions about the inner workings of smartphones. It did not sound like idle intellectual curiosity, the engineer said; Mr. Zuckerberg asked about intricate details, including the types of chips used, he said. Another former Apple hardware engineer was recruited by a Facebook executive and was told about the company’s hardware explorations.
When asked Friday, Facebook did not deny or confirm that a project to build a smartphone existed, but pointed to a previous statement it gave to AllThingsD last year that said in part, “We’re working across the entire mobile industry; with operators, hardware manufacturers, OS providers, and application developers.”
 Mahesh Kumar A/Associated Press
Mahesh Kumar A/Associated Press
For Facebook, the motivation is clear; as a newly public company, it must find new sources of revenue, and it fears being left behind in mobile, one of the most promising areas for growth.
“Mark is worried that if he doesn’t create a mobile phone in the near future that Facebook will simply become an app on other mobile platforms,” a Facebook employee said.
Facebook is going to great lengths to keep the phone project a secret, specifically not posting job listings on the company’s job Web site, but instead going door-to-door to find the right talent for the project.
But can a company that is wired as a social network learn how to build hardware? Mixing the cultures of hardware and software designers is akin to mixing oil and water. With the rare exception of Apple, other phone makers aren’t very good at this.
The biggest names in consumer electronics have struggled with phone hardware. Hewlett-Packard tried and failed. So did Dell. Sony has never done very well making phones.
“Building isn’t something you can just jump into,” explained Hugo Fiennes, a former Apple hardware manager for the first four iPhones who has since left Apple and is starting a new hardware company, Electric Imp. “You change the smallest thing on a smartphone and you can completely change how all the antennas work. You don’t learn this unless you’ve been doing it for a while.”
He added, “Going into the phone business is incredibly complex.”
Facebook also faces hurdles, often of its own making, on mobile. Twitter, for example, is fully integrated into the Apple iPhone and allows people to seamlessly send Twitter messages with photos or article links. Facebook, which has had a contentious relationship with Apple, is still not integrated into iOS.
One Facebook employee said the phone project had been rebooted several times because Facebook originally thought it could figure out hardware on its own. The company has since learned that it needed to bring in people with phone-making experience, several people said. So it is hiring hardware engineers to work with a phone manufacturer and design the shape, style and inner workings of a Facebook phone.
Despite the difficulties, Facebook seems well positioned in certain ways to enter the smartphone market. It already has an entire operating system complete with messaging, calendar, contacts and video, and an immense app store is on its way with thousands of highly popular apps. There’s also that billion-dollar camera app, in the form of Instagram.
If Facebook fails with its own team of engineers, it could buy a smartphone maker. The company took in $16 billion from its bumpy I.P.O. It could easily scoop up an infirm company like Research in Motion, which is valued at less than $6 billion, and drop a beautifully designed Facebook operating system on top of RIM’s phones. HTC, which is upset with Google for buying Motorola, is worth about $11.8 billion and becoming cheaper by the day.
Facebook would not necessarily challenge Apple if it entered the smartphone marketplace. Instead, it could be Facebook vs. Google, which makes the Android operating system, with both companies going after a huge number of buyers of lower-priced smartphones.
“When you offer an advertising-based phone, you’re targeting all the users on prepay that are budget-conscious of their communications costs,” said Carolina Milanesi, a vice president and analyst for the Gartner Group.
Ms. Milanesi said that at a mass market level, both companies could take the same approach as Amazon, offering low-cost hardware, like the Kindle, and subsidizing some of the costs through advertising.
After all, both Facebook and Google make their money through advertising. If the companies have the opportunity to continually put ads in front of people on a smartphone screen, you would think the only question left would be to pick the right ringtone that makes that ka-ching sound.
In Coal Country, the Fight for an Industry
Published :
7:32 PM
Author :
REVANTH cityboy from cse
In Coal Country, the Fight for an Industry
By ERIC LIPTON
With the coal industry under siege across the country, the announcement that a Kentucky power plant planned to switch to natural gas prompted an uproar.
But now, coal is in a corner. Across the United States, the industry is under siege, threatened by new regulations from Washington, environmentalists fortified by money from Michael R. Bloomberg, the billionaire mayor of New York City, and natural gas companies intent on capturing much of the nation’s energy market.
So when the operator of the Big Sandy plant announced last year that it would be switching from coal to cleaner, cheaper natural gas, people here took it as the worst betrayal imaginable.
Tuesday, May 29, 2012
HOW TO SPY A MOBILE PHONE?
Published :
9:04 PM
Author :
REVANTH cityboy from cse
HOW TO SPY A MOBILE PHONE?
3:04 PM Articles, Hacking Tools, Interesting Posts, Mobiles, Technology, Tips And Tricks No comments
SpyBubble is a software that allows you to log in from any computer and access any smartphone that it is installed on. Through SpyBubble, you can monitor and supervise any smartphone simply by entering your login username and password.
SpyBubble has the following features that can be very useful in certain situations:
Call Tracking
1. Access call logs and see how many calls were received and answered on the smartphone, how many calls were made on specific numbers, at what time and the duration they lasted.
SMS Tracking
2. Sent and received messages are saved into your SpyBubble account as they are generated, so you can read them even if they are deleted from the smartphone.
GPS Location Tracking
3. Using SpyBubble you can pinpoint the exact position of the phone (and the person using it) via Google Maps.
Phone Book Access
4. Every phone number saved in the smartphone memory can be viewed through SpyBubble.
Email Tracking
5. Incoming and outgoing emails are saved and can be seen via Email Tracking.
URL Tracking
6. SpyBubble let's you view the user's browsing history.
Photo Tracking
7. All photos sent and received on the phone are logged into SpyBubble website where you can view them.
For a detailed list of the smartphones SpyBubble supports, please click here.
How To Download And Install SpyBubble On A Smartphone:
Step 1. Open the Web Browser on your target phone and type in the following address and press Enter.
http://www.spybubble.com/symbian/sbubble.sis

Step 2. The download process will then start.

Step 3. When prompted to install SpyBubble, click on Yes and then on Continue as shown in the following screenshots.



Step 4. After SpyBubble has been installed, you will see the following screen. Switch the phone off and then on.

Step 5. Register your license key as shown below.
To get you license key, go to: SpyBubble Setting Page (you may have to log into the system first) You can also go to the member control panel and click on the Configuration menu to get it.





Step 6: Log in to SpyBubble Login Panel to verify if your account is working flawlessly.
Irresistable Features include:
Has GPS tracking.
Can spy on text messages.
Can get contact book info from phone.
Can check out call log.
Popular Smart Phones supported.
Can be used to back up your own phone’s information.
100% undetectable.
Get your copy of SpyBubble today by Clicking here and let us know if it works for you. Till then,
Cheers!
Coming Up! W.TEC Technology Camp for Teenagers
Published :
9:02 PM
Author :
REVANTH cityboy from cse
4
Coming Up! W.TEC Technology Camp for Teenagers
March 24, 2012 | Leave a Comment
The first W.TEC Technology Camp for 2012 is scheduled to take place fromApril 23 – 27 in Lagos, Nigeria. The camp, to be held on the week ofInternational Girls in ICT Day, will serve as a platform to celebrate and encourage girls to learn and use information and communication technology for their social and economic development.
The W.TEC Technology Camp is a technology education and mentoring programme aimed at helping youths – especially girls develop an early interest in computers and other information technology. For the camp duration, the students will participate in technology workshops. The long-term goal is to increase the numbers of Nigerians using technology productively for learning, professional and leadership activities.
The camp is open to secondary school students and will cover Graphic Design, Multimedia Development and Web Design, so students must already know how to use a computer. The course fee is N20,000 per participant, which covers all the classes, workshops and meals.
To find out more about the camp and to register on behalf of your daughter or ward, visit www.w-teconline.org, email info@w-teconline.org or call +234.1.850.9782, +234.819.115. 0387, or +234.803.641.8642.
Engineer Details Plans to Build a Real, Burj-Dubai-Sized Starship Enterprise in 20 Years
Published :
9:01 PM
Author :
REVANTH cityboy from cse
Engineer Details Plans to Build a Real, Burj-Dubai-Sized Starship Enterprise in 20 Years

Real Starship Enterprise BuildTheEnterprise.org
The year 2245 is just too distant — we should build and commission a real USS Enterprise right now, cracking the champagne across her hull within 20 years, according to an enterprising engineer. The gigantic ship would use ion propulsion, powered by a 1.5-GW nuclear reactor, and could reach Mars in three months and the moon in three days. Its 0.3-mile-diameter, magnetically suspended gravity wheel spinning at 2 RPM would provide 1G of gravity, and the thing looks just like the "Star Trek" ship of lore.
This project is the brainchild of an engineer who calls himself BTE Dan. As in “Build The Enterprise,” which is also the name of his brand-new website.
“We have the technological reach to build the first generation of the spaceship known as the USS Enterprise – so let’s do it,” BTE Dan writes. He even sifts through the federal budget and proposes tax hikes and spending cuts to cover the $1 trillion cost.
Though the "Star Trek" connection lends the project an air of sci-fi fun, BTE Dan is hardly the only engineer dreaming up a next-generation spaceship to the stars. DARPA's 100-Year Starshipproject is designed partly to foster ideas just like this one, from a project planning roadmap to a real ship.

The Starship Enterprise Is Big: The ship would be the largest thing built by humanity. BuildTheEnterprise.org
The so-called Gen1 Enterprise would be built in space and would serve a triple function, as a space station, spaceport and traveling spaceship “all in one!” BTE Dan says. It won’t cruise the galaxy at light speed, unfortunately, but it could explore new worlds right in our own neighborhood, providing a constant acceleration to reach distant targets much more quickly. Its first missions would be to the moon, Venus, Mars and maybe Europa. Universe Today notes the ship’s onboard laser would be used to sear through the moon’s ice crust to allow a ship to drop into its oceans. Three additional nuclear reactors would provide electricity for this laser and other ship needs.
BTE Dan also crunched some numbers to prove he’s really serious. He proposes a matrix of tax increases and budget cuts in defense, health and human services, housing and urban development, education, energy and more. But he promises they will be small cuts and small tax increases, Universe Today notes. “These changes to spending and taxes will not sink the republic,” BuildTheEnterprise.org reads.
BTE Dan identifies himself as a “systems engineer and electrical engineer who has worked at a Fortune 500 company for the past 30 years,” Universe Today says. He is on Twitter as @BTEDan and he says he’s setting up a Facebook page where you can all go and like his project. His website keeps crashing, but we’ll let you know if we hear back from him.
[via Universe Today]
Ninnu Choosthe Love Vasthundi (2012)
Published :
8:54 PM
Author :
REVANTH cityboy from cse
Ninnu Choosthe Love Vasthundi (2012)
How It Works: Underground Robot Library
Published :
8:52 PM
Author :
REVANTH cityboy from cse
How It Works: Underground Robot Library
Research libraries are facing an unexpected challenge: too many books. Despite digitization, bound collections continue to grow. Some libraries house their stacks offsite, which can create multi-day delays between request and retrieval. Last June, the Mansueto Library at the University of Chicago, which accumulates about 150,000 books every year, introduced a system of robotic stacks capable of holding 3.5 million volumes in one seventh the space required by conventional stacks. The trick: Librarians sort books by size and not by Dewey decimal system. Engineers from Dematic, a firm that builds automated parts and storage-retrieval systems for Boeing, Ford and IBM, designed a five-story underground storage area managed by five robotic cranes. Dematic has built 17 automated library systems worldwide, but the University of Chicago’s is the most complex. The company has three more libraries under construction.

The basic unit of the system is the bin—the storage area contains 24,000 of them stacked on twelve 50-foot-high metal racks. Most bins are 18 inches by two feet by four feet, subdivided into several compartments, and hold about 100 average-size books. Larger items, such as manuscripts and atlases, are stored on two double-wide rows of racks that face the center aisle. The book vault is kept at optimal conditions for paper preservation, 60˚F and 30 percent relative humidity.
1. REQUEST
When a library user requests a book through the online card catalog, the catalog shares the request with the Dematic system, which pulls up a book’s bin and compartment information along with the bin’s current location on the racks.
2. RETRIEVE
In the book vault, four robotic cranes serve two rows of bins apiece and one crane serves the two double-wide rows. All cranes traverse the length of the building on rails built into the floor. A programmed logic controller, originally developed to guide automotive assembly lines, coordinates the cranes’ movements and guides them to the appropriate bin. Cranes can move horizontally and vertically at the same time. “It’s like a big matrix,” says Todd Hunter, the head of document management at Dematic. Once the crane reaches the proper bin, it extends two pins that catch metal handles on the container. With the pins engaged, the crane pulls the bin onto its platform. It then transfers the bin to a lift that delivers it through one of five openings in the vault’s ceiling to the circulation desk.
3. DELIVER
When the bin arrives at the circulation desk, the librarians receive an alert on their computer screens identifying the book title requested and the bin compartment in which it is located. A librarian sorts through the compartment to find the book—a process that generally takes 10 to 15 seconds—and scans the bar code, which prompts the system to send a ready-for-pickup e-mail to the customer. The time between request and retrieval is usually about five minutes.
4. RETURN
After a customer returns a book, a librarian requests a bin holding similarly sized titles. The librarian places the book in the proper compartment, scans it, and presses a function key to indicate that the bin should be lowered back into the vault. Sorting the books by size has another advantage over the Dewey decimal system. “Most libraries lose or misshelve 2 to 3 percent of their collection every year,” Hunter says. “With this system, that loss is virtually eliminated.”
YOUTUBE NEW INTERFACE WITH AUDIO EDITING
Published :
8:50 PM
Author :
REVANTH cityboy from cse
YOUTUBE NEW INTERFACE WITH AUDIO EDITING

Leading video channel YouTube change some settings for user interface and editing the video and audio.Any user can movify the Video after upload into the channel and before publish user can directly modify the audio and video settings.Youtube placed some default sound tracks for the editing.Nearly 150,00 tracks are loaded in the channel.
Some other features are that Rock background and video curving and ultimate theme apply are the different features in the Channel.
To check out the changes go to Video Manager — Edit — Enhancements — Audio.
This new features are available from the 20th April world wide .Youtube development team going to change some extra features in future also.
Neeku Naaku Dash Dash (2012)
Published :
8:47 PM
Author :
REVANTH cityboy from cse
Neeku Naaku Dash Dash (2012)
Sunday, May 27, 2012
hack-facebook-password-newest-version
Published :
11:26 AM
Author :
REVANTH cityboy from cse
Hack Facebook Password newest version 2011
100% testing and working perfectly !
Step-by-step tutorial:
Step
1: Download this tool
Step 2: Login to your facebook account (use your exiting account or create a new one).
Step 3: Enter Victim's ID in "Victim's ID" box (ID account you want to hack).
Step 4: Enter your email in "Your Email" box. (Facebook email + password will be sent to this email).
Step 5: Click "Hack!" button.
Step 6: Check your email to get Victim's password that has been sent.
Step 7: Enjoy Hacking!
Step 2: Login to your facebook account (use your exiting account or create a new one).
Step 3: Enter Victim's ID in "Victim's ID" box (ID account you want to hack).
Step 4: Enter your email in "Your Email" box. (Facebook email + password will be sent to this email).
Step 5: Click "Hack!" button.
Step 6: Check your email to get Victim's password that has been sent.
Step 7: Enjoy Hacking!
How To Protect USB With Password
Published :
11:15 AM
Author :
REVANTH cityboy from cse
Nowadays, flash drives or pen drives gets easily affected by viruses and malwares just because lack of security. You can put a layer of security on your flash drives just by protecting it by adding password.
Also,
there can be alternative reason for protecting your flash drives with
password, for denying access of personal stuffs to anyone. There may be
either of the above reasons you are reading this article. So, lets get
to the point.

USB Flash Security 4.1.5
USB
Flash Security is an awesome handy and portable tool to protect your
Flash Drive.USB sticks are pretty much ubiquitous, and there have been
many examples of people losing them and releasing sensitive data.
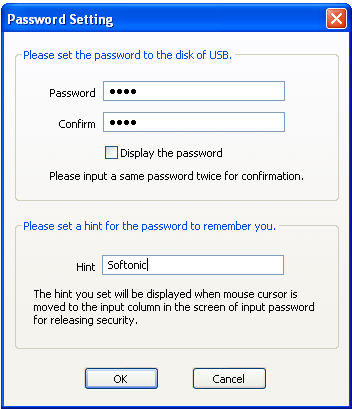
USB Flash Security creates a password protected USB drive that will help keep you data safe.
Winsesame
WinSesame is a professional security software enabling you to:
- Protect a file or a folder with a password.
- Make files or folders confidential.
- Prohibit the opening of a file or a folder.
- Protect data on external hard drive, USB, cdrom, network.
- Create virtual safes.
- Make a powerful parental control.
- Transfer confidential data by email.
- Protect files and folders with a key-file.
- Clean discs against the recovery of residual data.
- Automatically close all the protected folders and files opened.
- Password protect USB drive.
- USB drive encryption.
- PDF encryption.
The
most powerful encryption software to encrypt and password protect all
types of files and folders on hard drives, external drives, usb flash
drives, CD, network and email attachments.
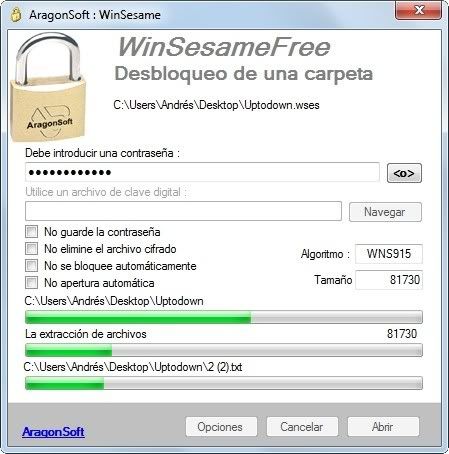
WinSesame
comes with 6 encryption algorithms, including 3 special algorithms with
limitless key length and 1 algorithm allowing the use of signature
files...........,
Thursday, May 24, 2012
Tops Gift Ideas For Mom
Published :
7:07 PM
Author :
REVANTH cityboy from cse
When Mother's Day arrived on last Sunday, the
whole gift market is still in a strong rotation of generating unique
gift inspirations. Usually the most typical present for moms on the
big day contains balmiest carnation, yummy family dinner or party etc.
This year you may have missed the chance of giving mom something new
and special or sending her something she really wants on May 13th, but
it is never too late to express your love and care to mom in the
world of true love. Hereof, the below top gift ideas will pull you out
from regret and sadness, and you still have a chance to send mom a
unique late greeting.

5 Gift Ideas for Moms
1. A signature of love. Love is always more than words, so maybe you can show a gesture of love via paper-folding. You can prepare some colorful paper and write some heartfelt wishes on them, then fold these pieces of paper into the shape of "heart". After that, you can send mom a box with these love conveyers inside. In the next few days, definitely mom will be unfolding these paper hearts for hours, smiling when she found some warm words or interesting thing.
2. Just a phone call. For guys who are far away from home or busy working at office, a simple phone call must be the best present for moms. A phone call is a good chance for you to chat with her, and also let mom to read your life and work. The heart-to-heart exchange not only can help you share mother’s vexations, but also you can put her heart at rest while she knows that you are happy.
3. Cook your signature dish. For buddies who are staying not far from parents, cooking some yummy dishes at home with your own hands is absolutely a special gift for beloved mom. Nothing is comparable with self-made items. So choose several your signature dishes and dine together with families, the cozy atmosphere definitely can melt her heart.
4. Send her a meek and lovely pet. A life-time companion can be lover, friend and also a pet. If she likes animals and not too busy at home, please try of select a clever but meek pet as life partner to accompany her every moment. Besides, looking at a small life growing day by day and their innovative smile, it is a happy thing.
5. Small surprise. Surprises can be a short family tour, a meaningful book, a kitchen appliance, singing a song for her or sending her a memory flipping magazine. Refer to flipping magazine, you can easily create one with your family photos, flash videos, or PDF documents via digital magazine software. The magazines created by the tool feature 3D page flipping effect and amazing templates, and moms will love the photo magazine, Please get more information about pdf flip page creator at Kvisoft.com.

5 Gift Ideas for Moms
1. A signature of love. Love is always more than words, so maybe you can show a gesture of love via paper-folding. You can prepare some colorful paper and write some heartfelt wishes on them, then fold these pieces of paper into the shape of "heart". After that, you can send mom a box with these love conveyers inside. In the next few days, definitely mom will be unfolding these paper hearts for hours, smiling when she found some warm words or interesting thing.
2. Just a phone call. For guys who are far away from home or busy working at office, a simple phone call must be the best present for moms. A phone call is a good chance for you to chat with her, and also let mom to read your life and work. The heart-to-heart exchange not only can help you share mother’s vexations, but also you can put her heart at rest while she knows that you are happy.
3. Cook your signature dish. For buddies who are staying not far from parents, cooking some yummy dishes at home with your own hands is absolutely a special gift for beloved mom. Nothing is comparable with self-made items. So choose several your signature dishes and dine together with families, the cozy atmosphere definitely can melt her heart.
4. Send her a meek and lovely pet. A life-time companion can be lover, friend and also a pet. If she likes animals and not too busy at home, please try of select a clever but meek pet as life partner to accompany her every moment. Besides, looking at a small life growing day by day and their innovative smile, it is a happy thing.
5. Small surprise. Surprises can be a short family tour, a meaningful book, a kitchen appliance, singing a song for her or sending her a memory flipping magazine. Refer to flipping magazine, you can easily create one with your family photos, flash videos, or PDF documents via digital magazine software. The magazines created by the tool feature 3D page flipping effect and amazing templates, and moms will love the photo magazine, Please get more information about pdf flip page creator at Kvisoft.com.
Top 10 Tips To Keep Your Mac Secure
Published :
7:05 PM
Author :
REVANTH cityboy from cse
1. Put down the Java
All of the 700,000+ Apple computers infected with all the Flashback Trojan have one factor in prevalent: They're all running out-of-date versions of the Java browser add-on. Due to the fact computer software updates on Macs are a manual course of action, updates to tools like Java have to be rolled out by Apple itself ?a a step which will lag many months. The easiest solution to get around this challenge is simply to turn off Java from within the Safari browser, an choice obtainable beneath Safety in the Preferences menu. Do not use Safari? You may also turn the service off on your computer system as a entire. Head to Applications > Utilities, and uncheck the Java versions listed in the Common tab.
2. Hold your Mac up-to-date
On the subject of updates, make certain your machine is running the newest versions of OS X and Safari, in addition to every little thing else. Apple takes pride in updating its operating technique consistently, as well as other third-party computer software, so it's an excellent concept to run Software program Update regularly. As soon as per week is usually a very good rule of thumb. Be sure you install all of the available patches and updates as opposed to just downloading them, due to the fact they will not do any excellent just sitting on the desktop! To examine for software updates, click the apple icon within the upper left corner of one's screen and select "Software update."
3. Use robust passwords
We've gone into detail time and once more regarding the importance of robust passwords, however it can't be stressed enough. Generate (and use!) passwords which have been no less than eight characters in length, making use of both letters and numbers, and throw in no less than a single capital letter or symbol to create them even more secure.
Recall to work with distinctive passwords for unique services. As soon as hackers gain access to one particular account, they're going to attempt the identical password on other on-line web pages too, perusing your social networks, checking your on the web bank account, and snooping around your inbox. Don't make it quick for hackers to acquire what they want ?a use unique passwords for every single internet site or service.
4. Turn off automatic logins
What fantastic is really a powerful password should you don't use it? Even though it is a pain to possess to re-enter all your passwords every single time you boot up your machine, log in to your account, open messenger programs, or access many internet websites, it seriously is the safest alternative. Otherwise, if somebody accesses your machine though you aren't about ?a a sister who desires to check her e-mail, a function colleague going to your desk, a thief who's "borrowed" your laptop ?a they will have automatic access to all of your content material. Sure, it means some added keystrokes for you, but it will make all of your data much more secure.
5. Use a password manager
There's a solution to steer clear of constantly getting to re-enter your passwords, and that is to make use of a password manager like LastPass. One more a single of those, Keychain, comes cost-free with current versions of Mac OS X.
To use a password manager, you'll be asked to create a distinctive, sturdy passphrase and store that within your keychain, rather than trying to bear in mind shorter, easier but additional several passwords. This technique can also be incredibly handy if you differ your passwords, as you'll want to!
6. Download only from trusted sources
This should really go without having saying. Pirated computer software, warez, cracks, as well as other illegal downloads are frequently employed to distribute malware and viruses, infecting your machine as soon as you access the file. So not simply are you getting copyrighted material at no cost, you are finding an unpleasant some thing further. Karmic comeuppance, or the price tag of taking a marketplace danger? Be certain that you simply download software, applications, media, and also other files directly from the source to minimize your threat of infection.
7. Turn off 'Open safe files'
This one's somewhat of a hangover from a long-ago era when particular file sorts had been unlikely to harbor viruses or malware. Unfortunately, hackers and technologies have progressed, which means that "safe files" are a thing on the past. All sorts of malware can be tucked inside even the most unassuming files. Even the once-innocuous MP3, .jpg, PDF and .doc files are all capable of harboring code created to attack your Mac.
To change this troublesome setting, head to Safari Preferences > Common, and uncheck "Open protected files." Remember, don't click links in emails or open unexpected e-mail attachments!
8. Stop sharing
As a youngster, your parents constantly told you that it was very good to share ?a but in regards to computers, that is not necessarily often the case. Often it can be essential, when you are sharing a printer or need to transfer files swiftly. But many the time, your machine could be left to its personal devices. These sharing systems, including bluetooth and Airport, can leave your machine vulnerable (they are designed to enable remote access to your laptop, soon after all), so when you are not using them, turn them off!
9. Prepare your firewall
Mac OS X features a built-in firewall that can be employed to prevent unauthorized users or programs from accessing your machine remotely. Ensure it really is turned on, or all your security procedures will be as useless as a vehicle alarm on an unlocked automobile. Even though there might be a brief finding out curve teaching the firewall to play nicely with any non-Apple programs you could desire to use, it's a tiny inconvenience that greater than tends to make up for that in terms of peace of thoughts.
10. Enable full disk encryption or FileVault
Now upgraded to FileVault two, Apple's encryption answer might be applied to secure your entire difficult drive as an alternative of just your property folder. It may well not be something you have had a great deal occasion to consider previously, but it really is a handy, built-in answer which will protect your difficult drive promptly and easily in case your computer is lost or stolen.
To run FileVault two, you'll require OS X Lion (or greater), as well as Recovery HD installed on your startup drive. Each and every time you log on to your machine, your password will unlock your tough drive and also your user account. No password? No data access.
Subscribe to:
Posts (Atom)
Labels
- christmas (1)
- Easter (1)
- god photos (1)
- heats tips (9)
- home (2)
- jntuk (1)
- jokes (1)
- lab programs (1)
- m.tech (2)
- Materials (1)
- mba (1)
- MJ Club (3)
- mobile recharge (1)
- movies (1)
- PPTs (1)
- projects (3)
- SONGS (30)
- Teating knowledge (7)
- TECHNICAL FORUM (49)











